La Matrice del Rischio Sicurezza ICAO Organizzazioni settore aeronautico / Doc 9859
| Appunti Sicurezza lavoro | |||||||||||||||||||||||||||||||||||||
| 16 Maggio 2025 | |||||||||||||||||||||||||||||||||||||
| Salve Visitatore | |||||||||||||||||||||||||||||||||||||
|
Matrice Rischio Sicurezza ICAO Organizzazioni settore aeronautico ID 22484 | 29.08.2024 / Attached ICAO Doc 9859 (EN) Safety Management Manual ICAO - International Civil Aviation Organization / Fourth Edition, 2018 (Doc 9859). Il Doc 9859 dell'ICAO è il Manuale di riferimento per la gestione dei rischi sicurezza di incidenti o sinistri aerei. Il metodo per la gestione dei rischi sicurezza (SMR) e la matrice del rischio (probability / severity), riportato al Cap 2.5 del Doc ICAO 9859 può trovare utile applicazione ad altre tipologie di rischi, quali quelli di sicurezza sul lavoro (vedasi anche ISO 31000). La gestione della sicurezza cerca di mitigare in modo proattivo i rischi per la sicurezza prima che si trasformino in incidenti e inconvenienti aerei. Attraverso l'implementazione della gestione della sicurezza, gli Stati possono gestire le proprie attività di sicurezza in modo più disciplinato, integrato e mirato. Avere una chiara comprensione del proprio ruolo e contributo alle operazioni sicure consente a uno Stato e al suo settore dell'aviazione di dare priorità alle azioni per affrontare i rischi per la sicurezza e gestire in modo più efficace le proprie risorse per il beneficio ottimale della sicurezza aerea. L'efficacia delle attività di gestione della sicurezza di uno Stato è rafforzata quando implementate in modo formale e istituzionalizzato attraverso un programma di sicurezza statale (SSP - State Safety Programme) e attraverso sistemi di gestione della sicurezza (SMS - Safety Management System) per i suoi fornitori di servizi. Il programma di sicurezza di uno Stato, combinato con gli SMS dei suoi fornitori di servizi, affronta sistematicamente i rischi per la sicurezza, migliora le prestazioni di sicurezza di ciascun fornitore di servizi e, collettivamente, migliora le prestazioni di sicurezza dello Stato. L'SSP è sviluppato e mantenuto da ogni Stato come un approccio strutturato per assistere nella gestione delle proprie prestazioni di sicurezza aerea. L'attuale record di sicurezza aerea è ottenuto attraverso un approccio tradizionale basato sulla conformità e dovrebbe continuare a essere trattato come il fondamento dell'SSP. Pertanto, gli Stati dovrebbero garantire di avere sistemi di supervisione della sicurezza efficaci. Ulteriori informazioni sull'SSP possono essere trovate nel Capitolo 8. Uno Stato deve richiedere che un SMS sia sviluppato e mantenuto da quei fornitori di servizi sotto la sua autorità, come identificato nell'Allegato 19 - Gestione della sicurezza, per migliorare costantemente le prestazioni di sicurezza identificando i pericoli, raccogliendo e analizzando i dati e valutando e gestendo costantemente i rischi per la sicurezza (vedere il paragrafo 1.2 per i dettagli sull'applicabilità dell'SMS). Ulteriori informazioni sull'implementazione di SMS sono disponibili nel Capitolo 9. Gli obiettivi del Global Aviation Safety Plan (GASP, Doc 10004) dell'ICAO richiedono agli Stati di mettere in atto sistemi di supervisione della sicurezza solidi e sostenibili e di evolverli progressivamente in un mezzo più sofisticato per gestire le prestazioni di sicurezza. Questi obiettivi sono in linea con i requisiti dell'ICAO per l'implementazione di SSP da parte degli Stati e di SMS da parte dei fornitori di servizi. Questo approccio alla sicurezza basato sulle prestazioni offre miglioramenti in quanto si concentra sul raggiungimento del risultato desiderato anziché concentrarsi esclusivamente sulla conformità o meno di uno Stato. È importante notare, tuttavia, che l'implementazione di un approccio alle prestazioni di sicurezza è collaborativa in quanto richiede uno sforzo da parte del settore dell'aviazione per sviluppare mezzi appropriati per raggiungere i risultati specificati e, per quanto riguarda gli Stati, per valutare l'approccio di ciascun fornitore di servizi. Un approccio alla sicurezza del sistema totale considera l'intero settore aeronautico come un sistema. Tutti i fornitori di servizi, e i loro sistemi per la gestione della sicurezza, sono considerati sottosistemi. Ciò consente a uno Stato di considerare le interazioni, e causa ed effetto, nell'intero sistema. Spesso è impossibile o poco pratico costruire tutti i sistemi di sicurezza nello stesso modo. Pertanto, una preoccupazione primaria per gli Stati e i fornitori di servizi è come gestire al meglio le interfacce tra sistemi interagenti dissimili. Quando si esamina l'applicabilità dell'SMS, è stato preso in considerazione il collegamento tra i fornitori di servizi che hanno già un requisito SMS ai sensi dell'Allegato 19 e altre organizzazioni che svolgono un'attività di aviazione. L'applicazione dell'SMS dovrebbe ridurre il rischio di lacune o sovrapposizioni di sicurezza, non aumentare il rischio di sicurezza attraverso una riduzione dell'interoperabilità. Quando un fornitore di servizi con un requisito SMS stipula un contratto con un'organizzazione non soggetta all'SMS, i pericoli e i rischi per la sicurezza potenzialmente introdotti dal contraente vengono affrontati dall'SMS del fornitore di servizi. Ciò impone ulteriori responsabilità di Safety Risk Management (SRM) al fornitore di servizi per garantire che siano informati sui rischi per la sicurezza indotti dalle attività dei loro appaltatori. Per maggiori informazioni su SRM, vedere il Capitolo 2. Estensione dell'applicabilità discrezionale dell'SMS I criteri di applicabilità delineati sopra possono anche servire come guida per gli Stati quando considerano un'estensione dell'applicabilità dell'SMS oltre quella definita nell'Allegato 19 o la promozione dell'implementazione volontaria. L'applicazione dell'applicabilità discrezionale di SMS dovrebbe essere attentamente considerata. La decisione di estendere l'applicabilità dell'SMS ai settori o ai fornitori di servizi dovrebbe tenere conto dei rischi per la sicurezza identificati nello Stato e, se la decisione viene presa, l'implementazione dell'SMS dovrebbe essere monitorata come parte dell'SSP. Prima di richiedere l'SMS, agli Stati viene chiesto di considerare se: a) ci sono altre opzioni valide per ottenere il miglioramento desiderato nelle prestazioni di sicurezza; e Ogni Stato dovrebbe considerare il livello accettabile di prestazioni di sicurezza (ALoSP) nel proprio settore e istituire uno schema di applicabilità dell'SMS che abbia maggiori probabilità di raggiungere gli obiettivi di sicurezza del proprio Stato. Lo schema di applicabilità dell'SMS applicato probabilmente evolverà in continuo allineamento con l'ALoSP dello Stato. Rischi congiunti sicurezza aerea e sicurezza e salute sul lavoro I rischi per la sicurezza associati a rischi composti che hanno un impatto simultaneo sulla sicurezza aerea e sulla sicurezza e salute sul lavoro possono essere gestiti tramite processi di mitigazione del rischio separati (paralleli) per affrontare rispettivamente le conseguenze separate per l'aviazione e la sicurezza e salute sul lavoro. In alternativa, può essere utilizzato un sistema integrato di mitigazione del rischio per l'aviazione e la sicurezza e salute sul lavoro per affrontare i pericoli composti. Un esempio di pericolo composto è un fulmine che colpisce un aeromobile al gate di transito di un aeroporto. TABLE OF CONTENTS Page Chapter 1. Introduction Chapter 2. Safety management fundamentals Chapter 3. Safety culture Chapter 4. Safety performance management Chapter 5. Safety data collection and processing systems Chapter 6. Safety analysis Chapter 7. Protection of safety data, safety information and related sources Chapter 8. State safety management Chapter 9. Safety management systems 2.5 SAFETY RISK MANAGEMENT Safety Risk Management (SRM) is a key component of safety management and includes hazard identification, safety risk assessment, safety risk mitigation and risk acceptance. SRM is a continuous activity because the aviation system is constantly changing, new hazards can be introduced and some hazards and associated safety risks may change over time. In addition, the effectiveness of implemented safety risk mitigation strategies must be monitored to determine if further action is required. 2.5.1 Introduction to hazards 2.5.1.1 In aviation, a hazard can be considered as a dormant potential for harm which is present in one form or another within the system or its environment. This potential for harm may appear in different forms, for example: as a natural condition (e.g. terrain) or technical status (e.g. runway markings). 2.5.1.2 Hazards are an inevitable part of aviation activities, however, their manifestation and possible adverse consequences can be addressed through mitigation strategies which aim to contain the potential for the hazard to result in an unsafe condition. Aviation can coexist with hazards so long as they are controlled. Hazard identification is the first step in the SRM process. It precedes a safety risk assessment and requires a clear understanding of hazards and their related consequences. 2.5.2 Understanding hazards and their consequences 2.5.2.1 Hazard identification focuses on conditions or objects that could cause or contribute to the unsafe operation of aircraft or aviation safety-related equipment, products and services (guidance on distinguishing hazards that are directly pertinent to aviation safety from other general/industrial hazards is addressed in subsequent paragraphs). 2.5.2.3 It is not uncommon for people to confuse hazards with their consequences. A consequence is an outcome that can be triggered by a hazard. For example, a runway excursion (overrun) is a potential consequence related to the hazard of a contaminated runway. By clearly defining the hazard first, one can more readily identify possible consequences. 2.5.2.4 In the crosswind example above, an immediate outcome of the hazard could be loss of lateral control followed by a consequent runway excursion. The ultimate consequence could be an accident. The damaging potential of a hazard can materialize through one or many consequences. It is important that safety risk assessments identify all of the possible consequences. The most extreme consequence - loss of human life - should be differentiated from those that involve lesser consequences, such as: aircraft incidents; increased flight crew workload; or passenger discomfort. The description of the consequences will inform the risk assessment and subsequent development and implementation of mitigations through prioritization and allocation of resources. Detailed and thorough hazard identification will lead to more accurate assessment of safety risks. Hazard identification and prioritization 2.5.2.5 Hazards exist at all levels in the organization and are detectable through many sources including reporting systems, inspections, audits, brainstorming sessions and expert judgement. The goal is to proactively identify hazards before they lead to accidents, incidents or other safety-related occurrences. An important mechanism for proactive hazard identification is a voluntary safety reporting system. Additional guidance on voluntary safety reporting systems can be found in Chapter 5. Information collected through such reporting systems may be supplemented by observations or findings recorded during routine site inspections or organizational audits. 2.5.2.6 Hazards can also be identified in the review or study of internal and external investigation reports. A consideration of hazards when reviewing accident or incident investigation reports is a good way to enhance the organization’s hazard identification system. This is particularly important when the organization’s safety culture is not yet mature enough to support effective voluntary safety reporting, or in small organizations with limited events or reports. An important source of specific hazards linked to operations and activities is from external sources such as ICAO, trade associations or other international bodies. 2.5.2.7 Hazard identification may also consider hazards that are generated outside of the organization and hazards that are outside the direct control of the organization, such as extreme weather or volcanic ash. Hazards related to emerging safety risks are also an important way for organizations to prepare for situations that may eventually occur. 2.5.2.8 The following should be considered when identifying hazards: a) system description; Occupational safety health and environment hazards 2.5.2.9 Safety risks associated with compound hazards that simultaneously impact aviation safety as well as OSHE may be managed through separate (parallel) risk mitigation processes to address the separate aviation and OSHE consequences, respectively. Alternatively, an integrated aviation and OSHE risk mitigation system may be used to address compound hazards. An example of a compound hazard is a lightning strike on an aircraft at an airport transit gate. This hazard may be deemed by an OSHE inspector to be a “workplace hazard” (ground personnel/workplace safety). To an aviation safety inspector, it is also an aviation hazard with risk of damage to the aircraft and a risk to passenger safety. It is important to consider both the OSHE and aviation safety consequences of such compound hazards, since they are not always the same. The purpose and focus of preventive controls for OSHE and aviation safety consequences may differ. Hazard identification methodologies 2.5.2.10 The two main methodologies for identifying hazards are: a) Reactive. This methodology involves analysis of past outcomes or events. Hazards are identified through investigation of safety occurrences. Incidents and accidents are an indication of system deficiencies and therefore can be used to determine which hazard(s) contributed to the event. b) Proactive. This methodology involves collecting safety data of lower consequence events or process performance and analysing the safety information or frequency of occurrence to determine if a hazard could lead to an accident or incident. The safety information for proactive hazard identification primarily comes from flight data analysis (FDA) programmes, safety reporting systems and the safety assurance function. 2.5.2.11 Hazards can also be identified through safety data analysis which identifies adverse trends and makes predictions about emerging hazards, etc. 2.5.2.12 Organizations should also identify hazards related to their safety management interfaces. This should, where possible, be carried out as a joint exercise with the interfacing organizations. The hazard identification should consider the operational environment and the various organizational capabilities (people, processes, technologies) which could contribute to the safe delivery of the service or product’s availability, functionality or performance. 2.5.2.13 As an example, an aircraft turnaround involves many organizations and operational personnel all working in and around the aircraft. There are likely to be hazards related to the interfaces between operational personnel, their equipment and the coordination of the turnaround activity. 2.5.3 Safety risk probability 2.5.3.1 Safety risk probability is the likelihood that a safety consequence or outcome will occur. It is important to envisage a variety of scenarios so that all potential consequences can be considered. The following questions can assist in the determination of probability: a) Is there a history of occurrences similar to the one under consideration, or is this an isolated occurrence? b) What other equipment or components of the same type might have similar issues? c) What is the number of personnel following, or subject to, the procedures in question? d) What is the exposure of the hazard under consideration? For example, during what percentage of the operation is the equipment or activity in use? 2.5.3.2 Taking into consideration any factors that might underlie these questions will help when assessing the probability of the hazard consequences in any foreseeable scenario. 2.5.3.3 An occurrence is considered foreseeable if any reasonable person could have expected the kind of occurrence to have happened under the same circumstances. Identification of every conceivable or theoretically possible hazard is not possible. Therefore, good judgment is required to determine an appropriate level of detail in hazard identification. Service providers should exercise due diligence when identifying significant and reasonably foreseeable hazards related to their product or service. Note. - Regarding product design, the term “foreseeable” is intended to be consistent with its use in airworthiness regulations, policy, and guidance. 2.5.3.4 Table 1 presents a typical safety risk probability classification table. It includes five categories to denote the probability related to an unsafe event or condition, the description of each category, and an assignment of a value to each category. This example uses qualitative terms; quantitative terms could be defined to provide a more accurate assessment. This will depend on the availability of appropriate safety data and the sophistication of the organization and operation.
Note. - This is an example only. The level of detail and complexity of tables and matrices should be adapted to the particular needs and complexities of each organization. It should also be noted that organizations might include both qualitative and quantitative criteria. 2.5.4 Safety risk severity 2.5.4.1 Once the probability assessment has been completed, the next step is to assess the severity, taking into account the potential consequences related to the hazard. Safety risk severity is defined as the extent of harm that might reasonably be expected to occur as a consequence or outcome of the identified hazard. The severity classification should consider: a) fatalities or serious injury which would occur as a result of: 1) being in the aircraft; b) damage: 1) damage or structural failure sustained by the aircraft which: 2) damage sustained by ATS or aerodrome equipment which: 2.5.4.2 The severity assessment should consider all possible consequences related to a hazard, taking into account the worst foreseeable situation. Table 2 presents a typical safety risk severity table. It includes five categories to denote the level of severity, the description of each category, and the assignment of a value to each category. As with the safety risk probability table, this table is an example only. Table 2. Example safety risk severity table
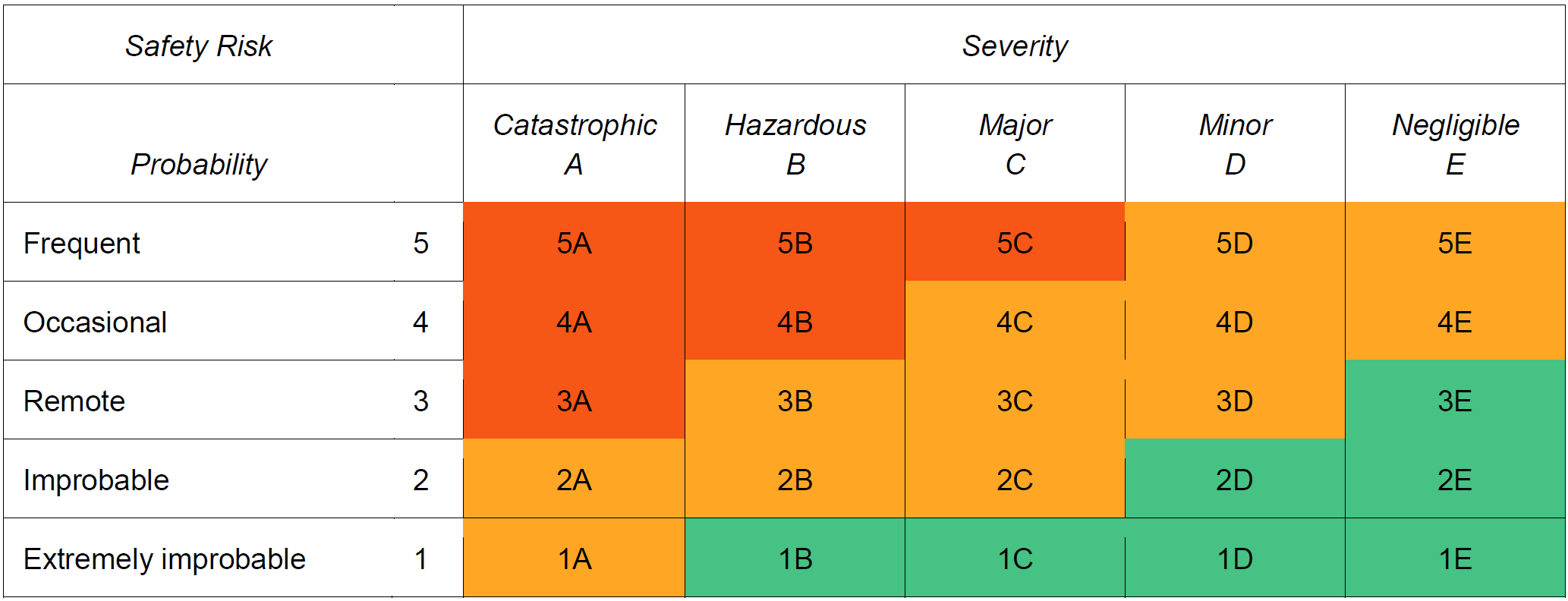
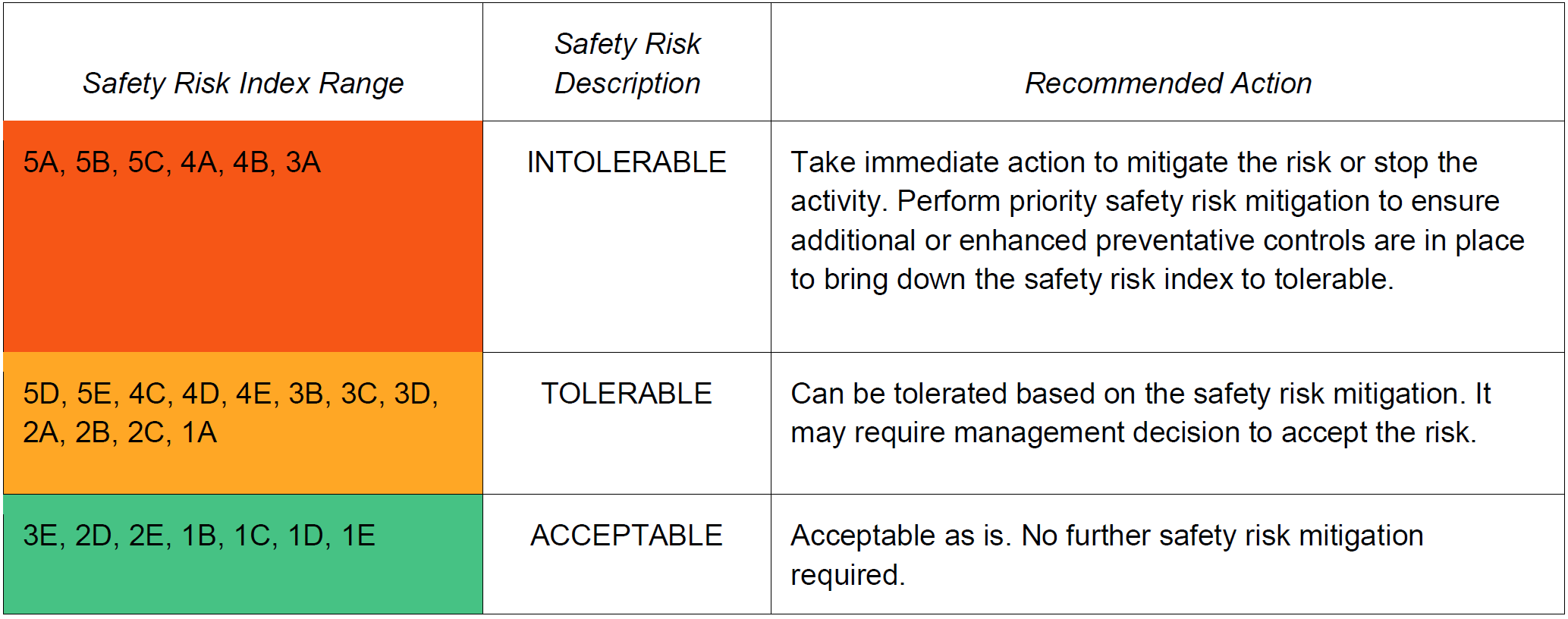
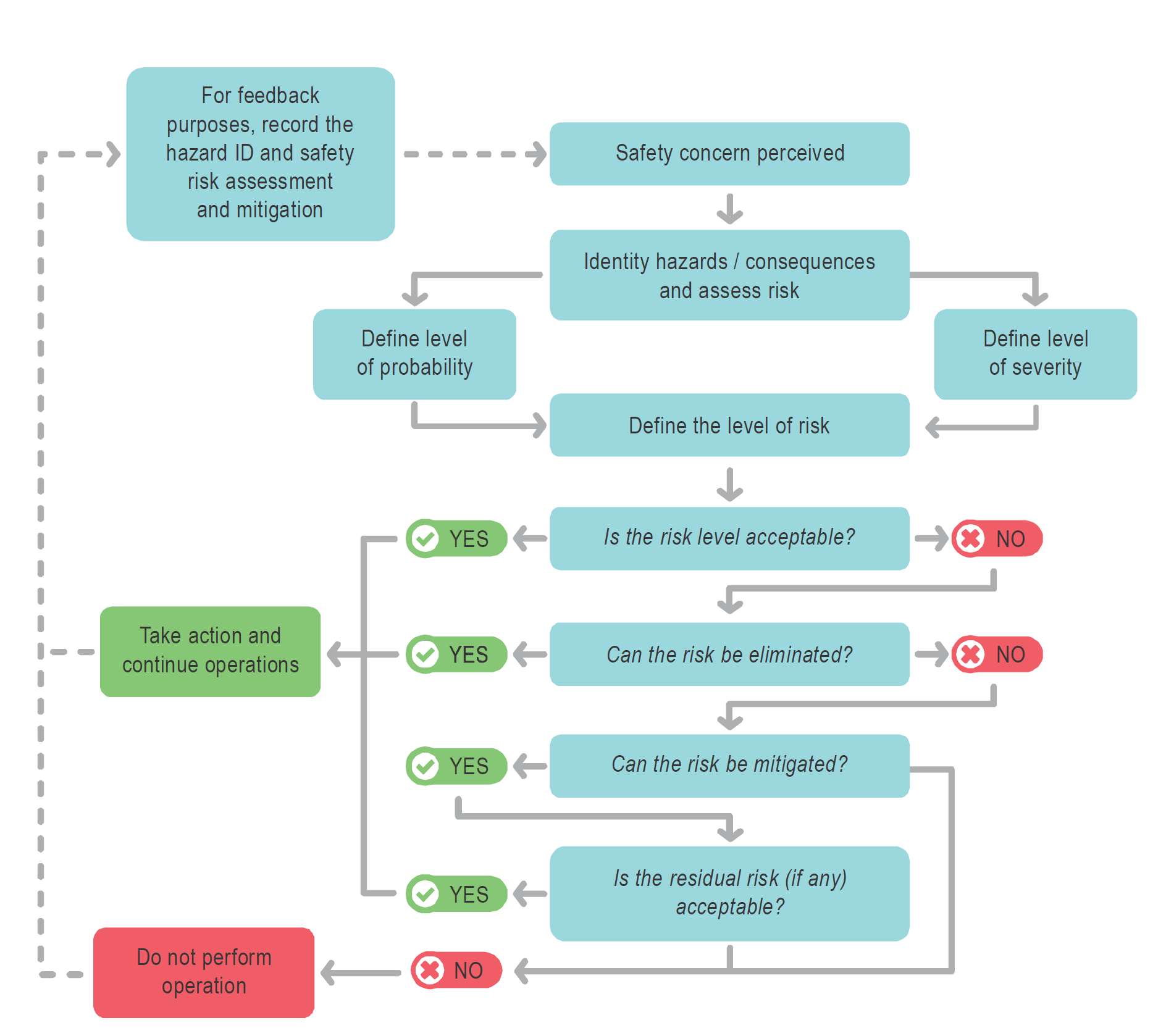
2.5.5 Safety risk tolerability 2.5.5.1 The safety risk index rating is created by combining the results of the probability and severity scores. In the example above, it is an alphanumeric designator. The respective severity/probability combinations are presented in the safety risk assessment matrix in Table 3. The safety risk assessment matrix is used to determine safety risk tolerability. Consider, for example, a situation where the safety risk probability has been assessed as Occasional (4), and the safety risk severity has been assessed as Hazardous (B), resulting in a safety risk index of (4B). Note. - In determining the safety risk tolerability, the quality and reliability of the data used for the hazard identification and safety risk probability should be taken into consideration. 2.5.5.2 The index obtained from the safety risk assessment matrix should then be exported to a safety risk tolerability table that describes — in a narrative form — the tolerability criteria for the particular organization. Table 4 presents an example of a safety risk tolerability table. Using the example above, the criterion for safety risk assessed as 4B falls in the “intolerable” category. In this case, the safety risk index of the consequence is unacceptable. The organization should therefore take risk control action to reduce: a) the organization’s exposure to the particular risk, i.e., reduce the probability component of the risk to an acceptable level; 2.5.5.3 Safety risks are conceptually assessed as acceptable, tolerable or intolerable. Safety risks assessed as initially falling in the intolerable region are unacceptable under any circumstances. The probability and/or severity of the consequences of the hazards are of such a magnitude, and the damaging potential of the hazard poses such a threat to safety, that mitigation action is required or activities are stopped. 2.5.6 Assessing human factors related risks 2.5.6.1 The consideration of human factors has particular importance in SRM as people can be both a source and a solution of safety risks by: a) contributing to an accident or incident through variable performance due to human limitations; b) anticipating and taking appropriate actions to avoid a hazardous situation: and c) solving problems, making decisions and taking actions to mitigate risks. 2.5.6.2 It is therefore important to involve people with appropriate human factors expertise in the identification, assessment and mitigation of risks. 2.5.6.3 SRM requires all aspects of safety risk to be addressed, including those related to humans. Assessing the risks associated with human performance is more complex than risk factors associated with technology and environment since: a) human performance is highly variable, with a wide range of interacting influences internal and external to the individual. Many of the effects of the interaction between these influences are difficult, or impossible to predict; and b) the consequences of variable human performance will differ according to the task being performed and the context. 2.5.7 Safety risk mitigation strategies 2.5.7.1 Safety risk mitigation is often referred to as a safety risk control. Safety risks should be managed to an acceptable level by mitigating the safety risk through the application of appropriate safety risk controls. This should be balanced against the time, cost and difficulty of taking action to reduce or eliminate the safety risk. The level of safety risk can be lowered by reducing the severity of the potential consequences, reducing the likelihood of occurrence or by reducing exposure to that safety risk. It is easier and more common to reduce the likelihood than it is to reduce the severity. 2.5.7.2 Safety risk mitigations are actions that often result in changes to operating procedures, equipment or infrastructure. Safety risk mitigation strategies fall into three categories: a) Avoidance: The operation or activity is cancelled or avoided because the safety risk exceeds the benefits of continuing the activity, thereby eliminating the safety risk entirely. b) Reduction: The frequency of the operation or activity is reduced, or action is taken to reduce the magnitude of the consequences of the safety risk. c) Segregation: Action is taken to isolate the effects of the consequences of the safety risk or build in redundancy to protect against them. 2.5.7.3 The consideration of human factors is an integral part of identifying effective mitigations because humans are required to apply, or contribute to, the mitigation or corrective actions. For example, mitigations may include the use of processes or procedures. Without input from those who will be using these in “real world” situations and/or individuals with human factors expertise, the processes or procedures developed may not be fit for their purpose and result in unintended consequences. Further, human performance limitations should be considered as part of any safety risk mitigation, building in error capturing strategies to address human performance variability. Ultimately, this important human factors perspective results in more comprehensive and effective mitigations. 2.5.7.4 A safety risk mitigation strategy may involve one of the approaches described above or may include multiple approaches. It is important to consider the full range of possible control measures to find an optimal solution. The effectiveness of each alternative strategy must be evaluated before a decision is made. Each proposed safety risk mitigation alternative should be examined from the following perspectives: a) Effectiveness. The extent to which the alternatives reduce or eliminate the safety risks. Effectiveness can be determined in terms of the technical, training and regulatory defences that can reduce or eliminate safety risks. b) Cost/benefit. The extent to which the perceived benefits of the mitigation outweighs the costs. c) Practicality. The extent to which mitigation can be implemented and how appropriate it is in terms of available technology, financial and administrative resources, legislation, political will, operational realities, etc. d) Acceptability. The extent to which the alternative is acceptable to those people that will be expected to apply it. f) Durability. The extent to which the mitigation will be sustainable and effective. g) Residual safety risks. The degree of safety risk that remains subsequent to the implementation of the initial mitigation and which may necessitate additional safety risk control measures. h) Unintended consequences. The introduction of new hazards and related safety risks associated with the implementation of any mitigation alternative. i) Time. Time required for the implementation of the safety risk mitigation alternative. 2.5.7.5 Corrective action should take into account any existing defences and their (in)ability to achieve an acceptable level of safety risk. This may result in a review of previous safety risk assessments that may have been impacted by the corrective action. Safety risk mitigations and controls will need to be verified/audited to ensure that they are effective. Another way to monitor the effectiveness of mitigations is through the use of SPIs. See Chapter 4 for more information on safety performance management and SPIs. 2.5.8 Safety risk management documentation 2.5.8.1 Safety risk management activities should be documented, including any assumptions underlying the probability and severity assessment, decisions made, and any safety risk mitigation actions taken. This may be done using a spread sheet or table. Some organizations may use a database or other software where large amounts of safety data and safety information can be stored and analysed. 2.5.8.2 Maintaining a register of identified hazards minimizes the likelihood that the organization will lose sight of its known hazards. When hazards are identified, they can be compared with the known hazards in the register to see if the hazard has already been registered, and what action(s) were taken to mitigate it. Hazard registers are usually in a table format and typically include: the hazard, potential consequences, assessment of associated risks, identification date, hazard category, short description, when or where it applies, who identified it and what measure have been put in place to mitigate the risks. 2.5.8.3 Safety risk decision-making tools and processes can be used to improve the repeatability and justification of decisions taken by organizational safety decision makers. An example of a safety risk decision aid is provided below in Figure 2-6. 2.5.9 Cost-benefit analysis Cost-benefit or cost-effectiveness analysis is normally carried out during the safety risk mitigation activities. It is commonly associated with business management, such as a regulatory impact assessment or project management processes. However, there may be situations where a safety risk assessment may have a significant financial impact. In such situations, a supplementary cost-benefit analysis or cost-effectiveness process to support the safety risk assessment may be warranted. This will ensure cost-effectiveness analysis or justification of recommended safety risk control actions has been taken into consideration, with the associated financial implications. Figure 2-6. Safety risk management decision aid Fonte: ICAO - International Civil Aviation Organization Collegati |
|||||||||||||||||||||||||||||||||||||
|
|
|||||||||||||||||||||||||||||||||||||
 |
|||||||||||||||||||||||||||||||||||||
|
è un sito di INVIO NEWSLETTTER Se vuoi cancellarti dall'invio della newsletter oppure effettua il login al sito ed entra nella Tua Area Riservata, in “Modifica dati” agisci con la spunta sul box di selezione “Newsletter”. L'Elenco completo di tutte le ns newsletter è qui: Archivio newsletter |
|||||||||||||||||||||||||||||||||||||
  |
|||||||||||||||||||||||||||||||||||||
| Certifico Srl 2000-2025 | VAT IT02442650541 | |||||||||||||||||||||||||||||||||||||